If your checkout is working and customers are paying, it’s easy to assume everything’s fine. But payment systems can be like a house with a strong front door and a cracked back window.
PCI DSS penetration testing is the controlled “break-in attempt” that shows you where the cracks are, before a criminal finds them. For founders, marketers, and small business owners, it’s not just a compliance box, it’s a practical way to reduce breach risk, protect revenue, and avoid ugly downtime.
This guide explains what PCI pen testing is, what PCI DSS 4.0 expects (as of December 2025), and how to run a test that actually improves security, not just paperwork.
PCI DSS penetration testing, explained in plain English
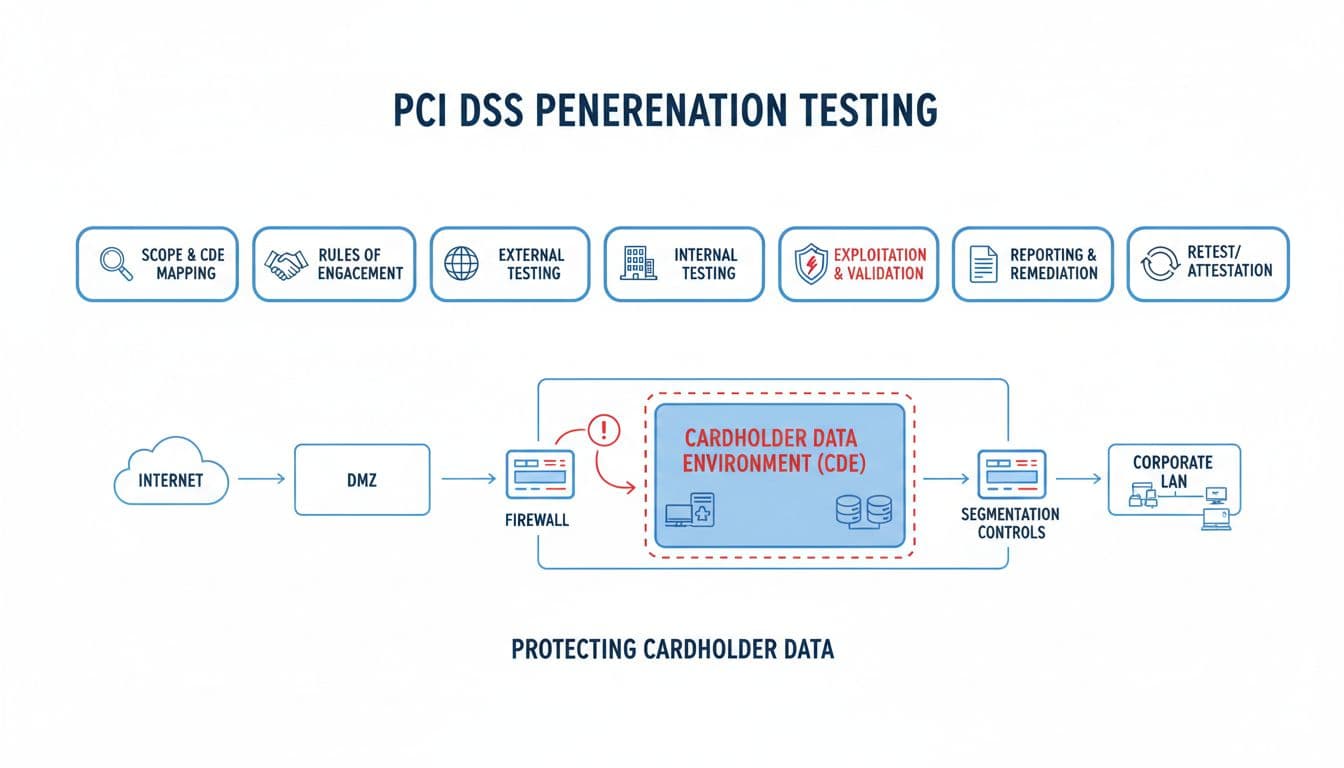
A PCI DSS penetration test is a targeted security test focused on the systems that store, process, or transmit card data, plus anything connected to them. PCI calls this the cardholder data environment (CDE).
Think of it like a health check for your payments stack. A vulnerability scan can tell you “you might have high blood pressure.” A penetration test tries to prove, safely and with permission, whether that weakness can be exploited in your real setup.
What it’s not: a random “try some hacks” exercise. A proper PCI test has scope, rules, evidence, and clear remediation steps.
For a deeper overview of the process, this step-by-step guide is a useful reference: PCI penetration testing step-by-step guide.
PCI DSS 4.0 requirements in 2025: what you must do (and when)
As of December 2025, PCI DSS 4.0 has moved past its transition window. The March 31, 2025 deadline has passed, so organizations handling card payments should already be meeting the updated expectations. Minor updates in 4.0.1 clarified wording, but didn’t introduce entirely new requirements.
At a high level, PCI expects both external and internal penetration testing, at least annually, and also after significant changes (new firewall rules, new payment app, new cloud environment, major routing changes, segmentation changes, and similar shifts).
The PCI Security Standards Council’s official supplement is still one of the clearest references for how PCI thinks about pen testing: PCI SSC penetration testing guidance (PDF). For practical auditor-facing questions, this is also helpful: PCI DSS penetration testing FAQ.
Here’s a quick way to frame it:
| Test area | What it targets | Typical trigger |
|---|---|---|
| External pen test | Internet-facing systems, exposed services, web apps, VPNs | At least annually, and after major changes |
| Internal pen test | Internal network paths, user-accessible systems, lateral movement | At least annually, and after major changes |
| Segmentation testing | Proof that non-CDE networks can’t reach the CDE | When using segmentation to reduce scope, plus changes |
Scoping the CDE: the part that saves money (and prevents surprises)
Most PCI test pain starts with scope confusion.
If your business uses a hosted checkout and tokens never touch your servers, your CDE may be small. If your app receives card data directly, even briefly, your CDE may be bigger than you think.
A good scoping session usually includes:
CDE mapping: Where does card data enter, where does it go, what logs it, what can access it?
System inventory: Web apps, APIs, admin panels, jump boxes, CI/CD, cloud accounts, third-party services.
Segmentation claims: If you say “the corporate LAN can’t reach the CDE,” the test must validate that.
If you process payments through a provider, it helps to understand where their responsibility ends and yours begins. This overview can help teams align on shared responsibility and PCI expectations: Stripe PCI compliance overview.
Internal vs external PCI pen testing: why you need both
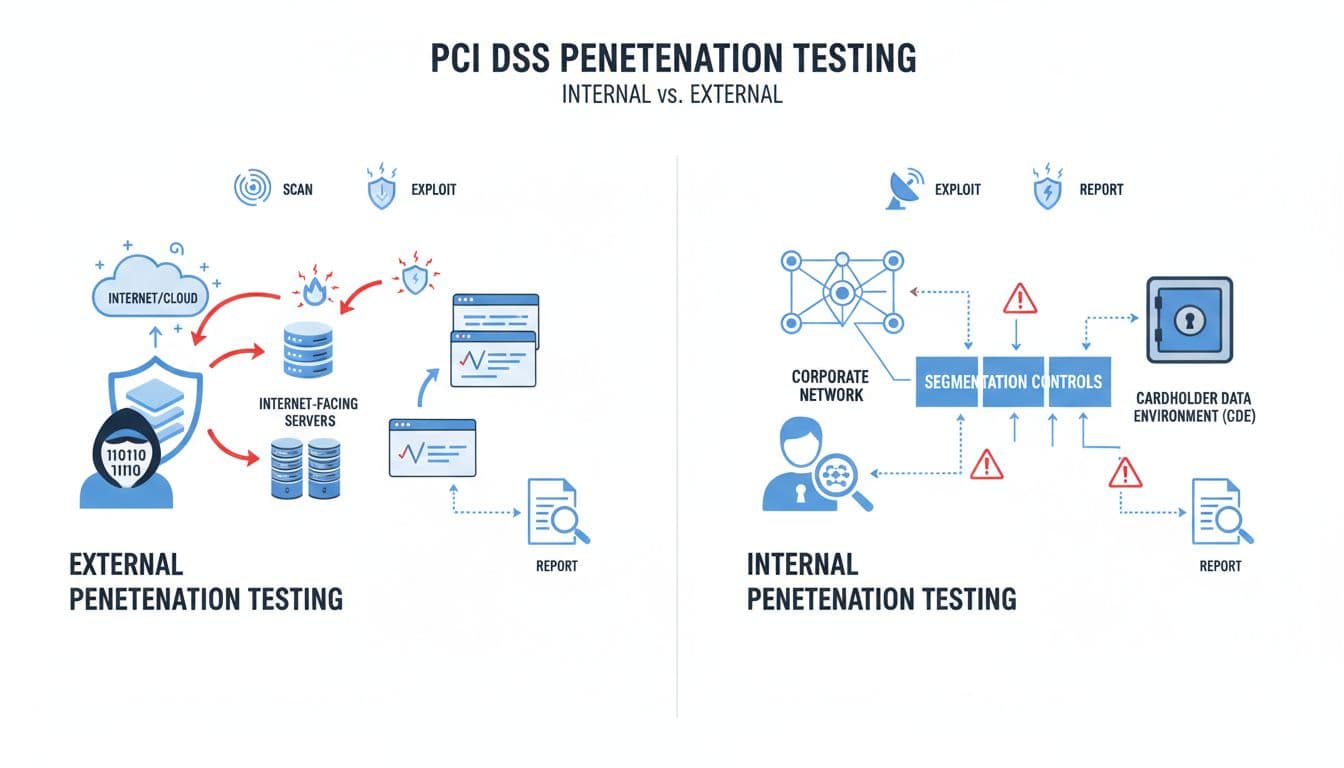
External testing answers: “Can an outsider break in from the internet?”
Internal testing answers: “If someone gets inside (phished user, infected laptop, rogue vendor access), can they reach payment systems?”
Real-world example: an ecommerce brand locks down its storefront, but the corporate network has a forgotten admin tool with a weak password. An attacker lands on an employee device, then moves laterally until they find the path to CDE systems. External testing might miss that. Internal testing catches it.
What a PCI DSS penetration test should include (so it doesn’t become theater)
A credible PCI test usually follows a repeatable flow:
Rules of engagement that protect your business
You’ll agree on testing windows, no-go systems, allowed techniques, and how incidents are handled. This avoids “we broke prod on Cyber Monday” scenarios.
Targeted testing and validation
Expect a mix of discovery, exploitation attempts (controlled), and validation of impact. For web apps, that can include auth issues, session handling, injection risks, and access control gaps. For networks, it often includes misconfigurations, weak segmentation, exposed management ports, and privilege escalation paths.
Evidence-rich reporting
A useful report isn’t a long list of CVEs. It explains:
- What was found, and why it matters
- How it was exploited (or why it’s exploitable)
- What data or systems could be impacted
- Clear fixes, with priorities
- Retest results after remediation
If you want another PCI DSS 4.0 oriented breakdown of requirements and reporting expectations, this guide is a strong supplement: PCI penetration testing requirements and process.
Common PCI pen test findings (and quick fixes that usually work)
Many issues repeat across SaaS, ecommerce, and service businesses:
Segmentation failures: “Guest Wi-Fi can reach CDE subnets.”
Fix: tighten firewall ACLs, remove any-to-any rules, restrict management ports, retest.
Over-permissioned identities (cloud IAM, admin accounts, shared credentials).
Fix: least privilege, MFA, remove stale accounts, isolate break-glass access.
Web app access control gaps (IDOR, missing object checks, weak admin controls).
Fix: server-side authorization checks, test with role-based scenarios, add logging.
Exposed admin surfaces (databases, dashboards, kubernetes panels).
Fix: put admin behind VPN, allowlist, or private endpoints, monitor access.
For businesses choosing payment providers or merchant accounts, security and compliance features vary a lot. If you’re comparing options, this overview can help you sanity-check the basics: choosing a secure merchant account for online sales.
Choosing the right tester (and preparing without panic)
The tester matters because PCI testing isn’t just technical. It’s also documentation, defensible scope, and clean retesting.
Look for:
Independence: Avoid conflicts of interest with the team that built the system.
Proof of method: Ask how they validate exploitation, not just scan.
Clear deliverables: Findings, evidence, remediation guidance, and retest.
Preparation checklist (simple, but effective):
- Confirm your CDE diagram and asset inventory are current.
- Lock in testing windows and escalation contacts.
- Create test accounts with realistic roles (customer, support, admin).
- Snapshot critical systems or ensure rollback plans exist.
- Decide how you’ll track fixes (ticketing, owners, deadlines).
If your CDE sits in the cloud, your shared responsibility model and network design can change the test approach. This comparison can help teams think through security trade-offs when hosting regulated workloads: cloud platform compliance and cybersecurity.
Conclusion: compliance is the floor, confidence is the goal
PCI DSS penetration testing is like a fire drill for your payment environment. You’re not hoping for a fire, you’re proving you can contain one.
Done well, it sharpens your CDE scope, validates segmentation, and turns vague security concerns into fixable work. If you handle card payments, schedule the annual test, retest after major changes, and use the report as a roadmap, not a filing cabinet document.
Want your next test to be easier and cheaper? Start by tightening scope and documenting your CDE, then treat PCI DSS penetration testing as an improvement cycle you repeat, not a once-a-year scramble.

Adeyemi Adetilewa leads the editorial direction at IdeasPlusBusiness.com. He has driven over 10M+ content views through strategic content marketing, with work trusted and published by platforms including HackerNoon, HuffPost, Addicted2Success, and others.
