A takeover doesn’t announce itself with a siren. It shows up as a small mismatch, a weird login, a sudden withdrawal request, and a support ticket that sounds normal.
That’s why iGaming account takeover response has to be structured. When money can move in minutes, “we’ll look into it” turns into chargebacks, player complaints, and a messy reconciliation sprint.
This guide lays out a practical triage SOP, the device and session clues that matter, the login patterns that often give attackers away, and the exact moments when freezing withdrawals is the safest call.
A triage SOP that works when everything is moving fast
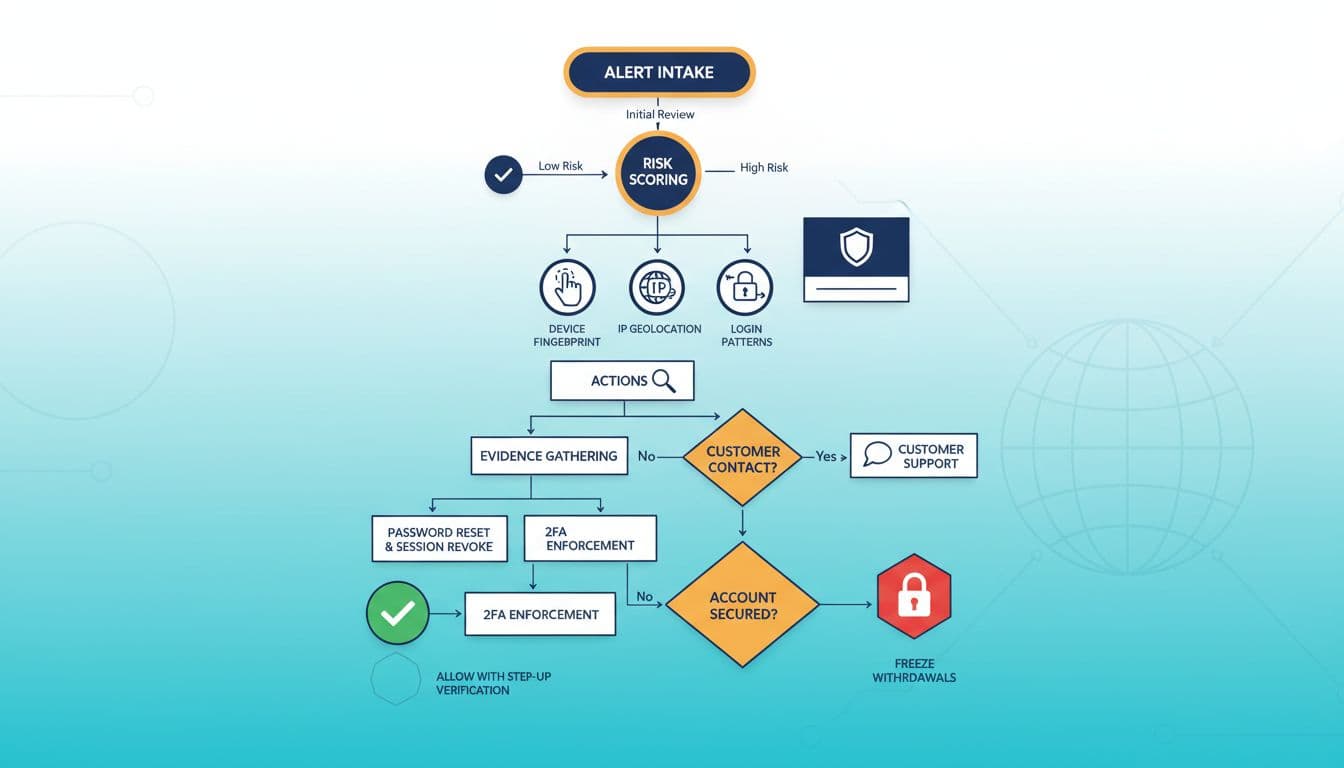
An ATO triage flow from alert to action, created with AI.
Think of triage like an ER intake desk. You’re not diagnosing everything at once, you’re deciding what’s urgent, what’s stable, and what needs containment right now.
1) Intake: capture the “who, what, when” in one screen
Start by standardizing the alert record. Whether it’s a player report, a risk engine flag, or a payment provider warning, capture:
- Account ID, VIP status, and current balance
- Latest login time, device, IP, ASN, and geo
- Recent changes: email, phone, password, 2FA, payout method
- Withdrawal attempts (amount, destination, status)
- Any linked accounts (same device, payment token, affiliate tag)
If you want a clean model for turning signals into evidence, the iGaming fraud signals-to-evidence hierarchy is a useful way to frame what you’re seeing.
2) Contain first, then investigate
Containment is about stopping the blast radius without locking out legitimate players unnecessarily.
A common containment sequence:
- Revoke active sessions (all devices), rotate refresh tokens
- Force password reset, then step-up authentication (2FA or verified link)
- Put a temporary hold on withdrawals if risk is medium or higher
If the player is active in-session, don’t debate it in chat. Trigger secure recovery and keep the account stable.
3) Evidence bundle: build a “case file” in 10 minutes
Your goal is a decision-ready bundle, not a 3-hour investigation. Pull:
- Device fingerprint history (first seen, last seen, change rate)
- IP history (country changes, data center flags, proxy signals)
- Login outcomes (fails, success, MFA prompts, recovery attempts)
- Gameplay behavior shift (bet size, game type, speed, session length)
- Payments and cash-out changes (new destination, new instrument)
4) Customer contact: one secure script, not free-form back-and-forth
Use a short, consistent script that avoids tipping off an attacker. Confirm:
- last known login device type and approximate location (city-level)
- last deposit method and approximate amount
- recent account changes they recognize (email/phone/2FA)
If answers don’t match your telemetry, treat it as a likely takeover.
Device clues and login patterns that separate takeovers from false alarms
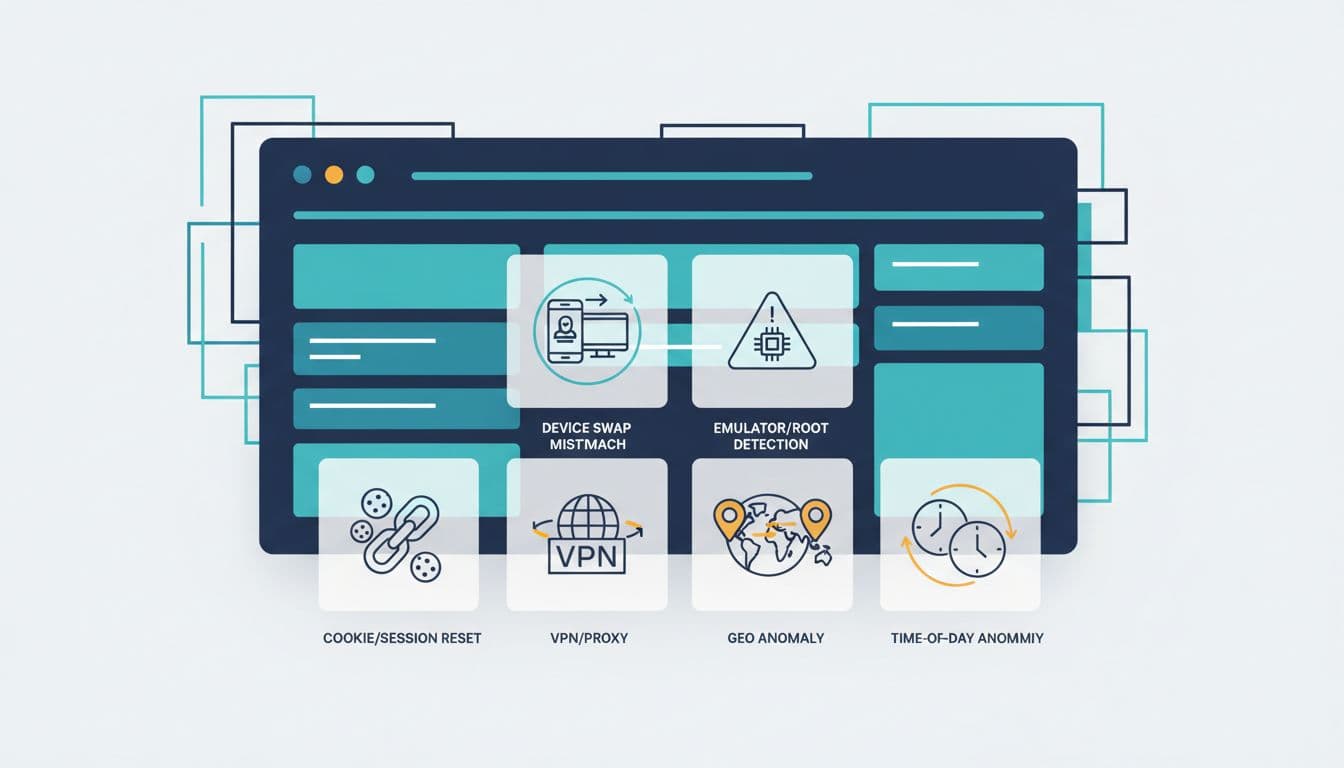
Common device and session clues risk teams use during ATO checks, created with AI.
False positives happen. People travel, replace phones, and forget passwords. The difference is usually in the shape of the data.
Device and session clues to weigh heavily
Strong takeover indicators tend to cluster:
- New device plus new network: a first-seen device on a never-seen ASN is more concerning than just a new phone.
- Emulator or rooted signals: not always fraud, but high-risk for money movement.
- Cookie reset right before cash-out: “fresh session” behavior can mean the attacker cleared storage to avoid linking.
- Multiple accounts touching the same device fingerprint: classic mule or testing pattern.
- Support channel switch: a player who normally emails now pushes urgent live chat, or asks to “change email quickly.”
A lot of these controls sit on top of a broader identity and access foundation. If you’re building that foundation now, it’s worth aligning with zero trust thinking and cloud identity controls, see key cloud security trends for 2025 for practical themes that translate well into fraud operations.
Login patterns that show intent (not just weirdness)
Here are patterns that often show an attacker’s workflow:
- Credential stuffing burst: many failed logins across accounts, then one success, then immediate profile navigation.
- Impossible travel: successful logins from far-apart regions within a short window (especially when one IP is a known proxy range).
- MFA friction: repeated “send code again” actions, failed OTP entries, or a sudden 2FA disable attempt.
- Fast pivot to high-impact pages: profile, payout methods, withdrawals, responsible gaming limits.
For broader, platform-agnostic detection ideas, SEON’s breakdown of how to detect account takeover fraud maps well to iGaming, especially when you translate it into “what changes right before money moves.”
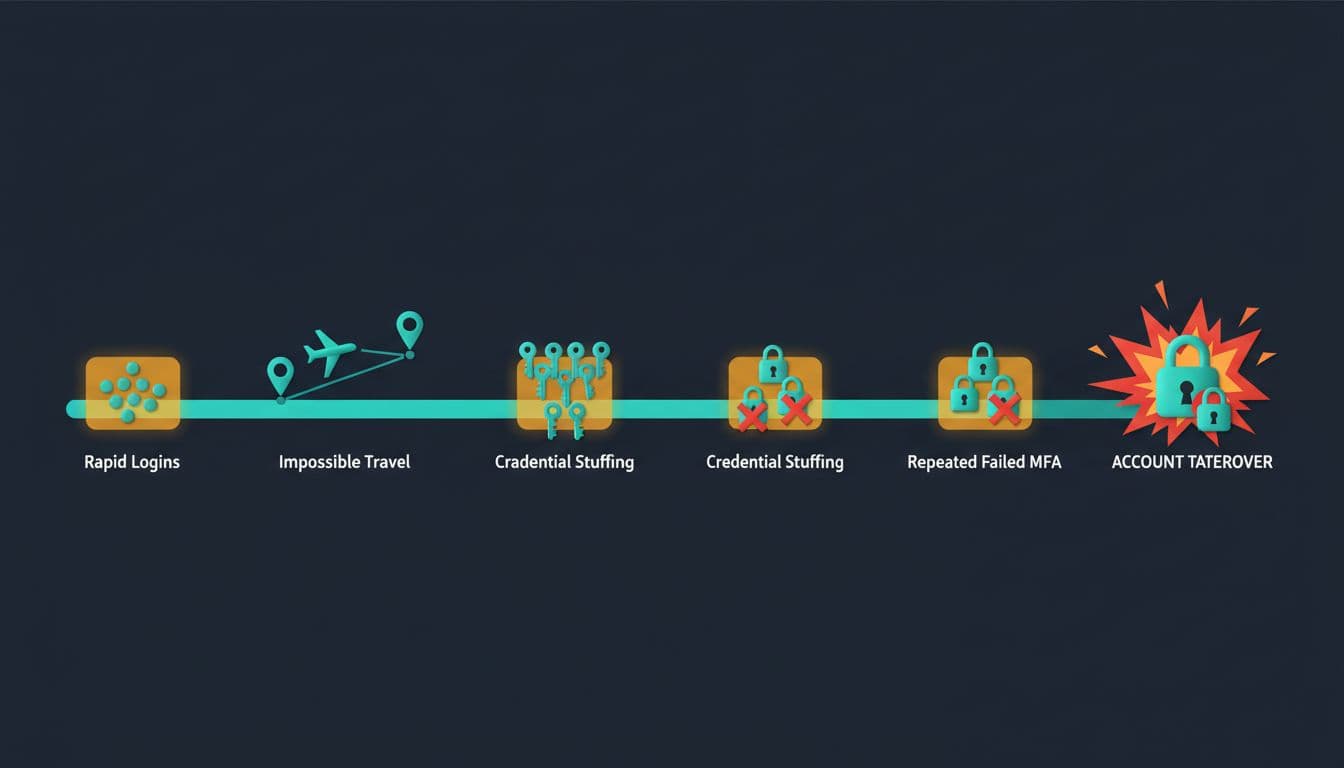
How suspicious login activity often clusters over time, created with AI.
When to freeze withdrawals (and how to do it cleanly)
Freezing withdrawals shouldn’t feel like panic. It should feel like a seatbelt: automatic when the risk is real, and documented when you click it.
A simple rule: if you can’t confidently prove control of the account, don’t let funds leave.
Practical withdrawal-freeze criteria (risk signals vs action)
Use a risk matrix that ties directly to evidence, not gut feel:
| Risk signals observed | Typical scenario | Action to take |
|---|---|---|
| New device only, player passes step-up | New phone, normal behavior | Allow withdrawal after step-up and session reset |
| New device + new geo/IP + profile change | Takeover attempt in progress | Freeze withdrawals, revoke sessions, force reset + 2FA |
| Multiple failed logins, then success + payout edit | Credential stuffing success | Freeze, lock payout edits, require enhanced verification |
| Chargeback history or linked-account anomalies + cash-out | Coordinated abuse or mule use | Freeze, escalate to fraud lead, consider AML review |
How to freeze without creating a support fire
- Freeze only the money-out path when possible, let gameplay and deposits remain available if it’s safe.
- Add a time-bound message in the account: “Withdrawal temporarily paused while we confirm account access.”
- Require a step-up that’s hard to social-engineer: verified email link plus device re-binding, or documented identity checks for higher risk.
This connects to payments governance too. If your team touches card flows and payout rails, your controls should align with compliance expectations, see this Stripe PCI compliance overview for a clear explanation of what “secure handling” looks like in practice.
For a higher-level view of ATO prevention and response options that can inform your playbooks, Feedzai’s account takeover fraud prevention guide is a solid reference point.
Conclusion
The fastest teams aren’t the ones who guess right every time. They’re the ones with a repeatable SOP, a short list of device and login signals they trust, and a clear line for when to pause money-out.
Build your triage workflow, train it with real cases, and audit every freeze decision for consistency. Done well, iGaming account takeover response becomes calmer, faster, and easier to scale as your player base grows.

Adeyemi Adetilewa leads the editorial direction at IdeasPlusBusiness.com. He has driven over 10M+ content views through strategic content marketing, with work trusted and published by platforms including HackerNoon, HuffPost, Addicted2Success, and others.
