Tournament prizes can be a magnet. They attract loyal players, but they also attract people who try to slip past the rules. If you run tournaments, iGaming tournament verification isn’t just a compliance box, it’s the difference between a clean leaderboard and a support queue on fire.
For founders, marketers, and operators, this is also one of the most practical business ideas in regulated gaming: build trust at scale. The goal is simple, treat every entry like an airport boarding pass. Right person, right place, right time, with proof you can show later.
What “iGaming tournament verification workflow” really covers
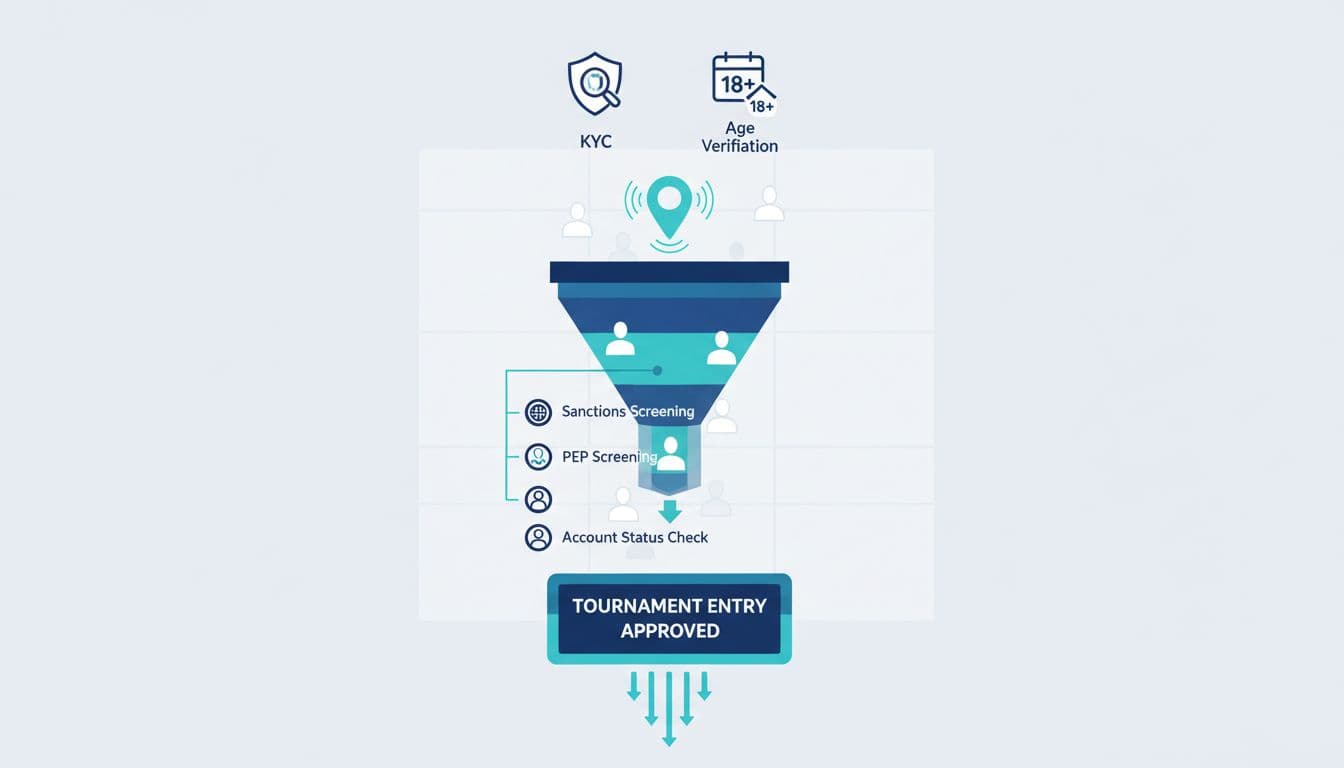
A tournament verification workflow is the set of checks and records that answer two questions:
- Is this player eligible to enter right now?
- If something goes wrong, can we prove what happened and resolve it fairly?
It’s not one check. It’s a chain of controls tied to three moments: tournament entry, gameplay, and payout.
If you want a deeper look at how teams prepare for inspections, this iGaming KYC audit guide is a helpful companion for aligning checks with regulator expectations.
Player eligibility checks (the gate before the leaderboard)
Eligibility checks should be consistent, fast, and hard to game. Most operators group them into identity, location, status, and integrity checks.
1) Identity and age (KYC basics, done at the right time)
At minimum, you need confidence that the account belongs to a real person of legal age. This can be “verify at registration,” or “verify before first withdrawal,” but tournaments often justify earlier checks because prizes and fraud risk spike.
Good KYC design balances speed and certainty. Vendors and guidance on gaming ID checks can help you avoid common mistakes, see GBG’s overview of ID verification in gaming.
What to store as evidence: verification result, timestamp, method, document metadata (not raw images everywhere), and any manual override notes.
2) Geolocation and jurisdiction rules (where the player is matters)
Tournament eligibility often depends on where the player is physically located, not just where they registered. Your workflow should check location at entry and again near payout if rules require it.
Regulatory requirements vary, but many markets set clear expectations around player controls and account rules. For an example of how a jurisdiction documents interactive gaming player requirements, see the Pennsylvania interactive gaming player rules.
Operational tip: when a location check fails, don’t just block. Log the reason, surface a clear message, and open a path for support review.
3) Sanctions and PEP screening (risk you don’t want)
If your tournaments include larger prizes, screening becomes more than a formality. A practical workflow triggers:
- Screening at onboarding (first deposit is common)
- Re-screening on key events (big deposits, big wins, payout request)
- Enhanced checks for higher-risk profiles
If you use a third-party identity solution, make sure it supports lifecycle checks, not just onboarding. Some vendors explain these lifecycle needs clearly, for example Mitek’s identity verification for iGaming.
4) Account status checks (the simplest thing that’s often missed)
Before tournament entry, your rules engine should confirm:
- Account isn’t self-excluded or time-out restricted
- Account isn’t suspended for fraud review
- Payment method limits or chargeback flags don’t block participation
- Bonus restrictions don’t conflict with tournament terms
This is basic, but it prevents the ugly scenario where a player competes, then you block payout because the account shouldn’t have been eligible.
5) Fair play checks (bots, collusion, multi-accounts)
Tournaments create incentives for coordinated play and automation. Your workflow should include signals like:
- Device and account linkage (shared devices, shared payment fingerprints)
- Gameplay pattern flags (improbable reaction times, repeated synchronized actions)
- Multi-account indicators (rapid signups, similar profiles, shared IP patterns)
When you do remove players, you’ll be challenged. That means your detection logic must create explainable evidence, not just a score.
A simple verification checklist you can hand to ops
This table helps teams align on what each check proves and what to retain for audit and disputes.
| Check type | What it confirms | Evidence to retain |
|---|---|---|
| Identity and age | Player is real and of legal age | Result, timestamp, provider response ID, override notes |
| Geolocation | Player is in an allowed place | Pass/fail, method, timestamp, confidence score |
| Sanctions/PEP | Player isn’t a restricted party | Match status, list version date, reviewer notes |
| Account status | Player is allowed to play | Status snapshot at entry and payout |
| Fair play | Competition integrity | Flags, model reasons, linked entities, case summary |
Automating the workflow without losing control
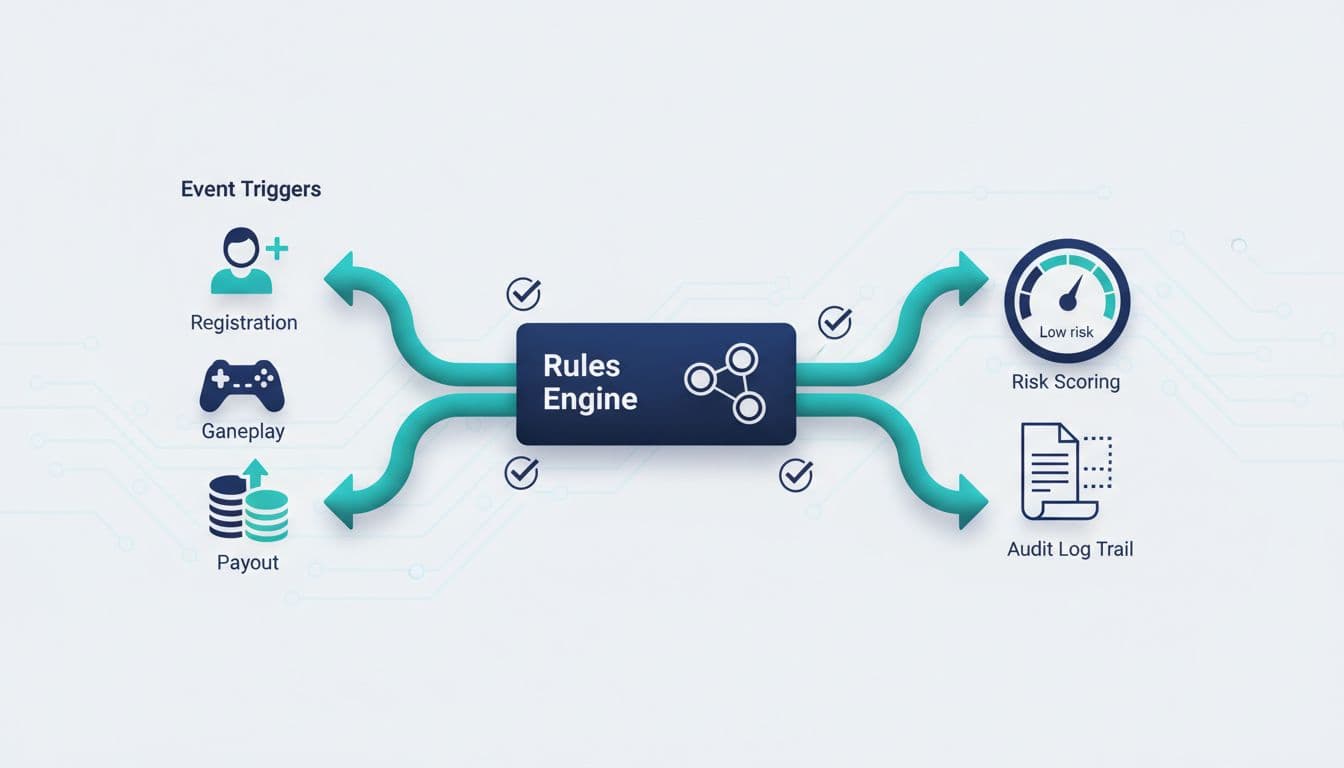
Automation is what keeps verification from becoming a bottleneck, but automation without logging is a liability. Every tournament decision should produce an audit trail that answers: what rule fired, what data was used, who approved, and when.
A reliable workflow usually looks like this:
Event triggers: registration, tournament entry, suspicious gameplay, payout request
Rules engine: eligibility rules, risk thresholds, exception routing
Outcome: allow, block, allow with review, hold payout
Audit log: immutable record of inputs, rule versions, decisions, and communications
If you’re preparing license materials, it helps to document these controls clearly in your policies and exhibits. This guide on iGaming license compliance docs is useful for packaging the workflow in a regulator-friendly format.
Dispute resolution steps (what happens when players challenge a result)
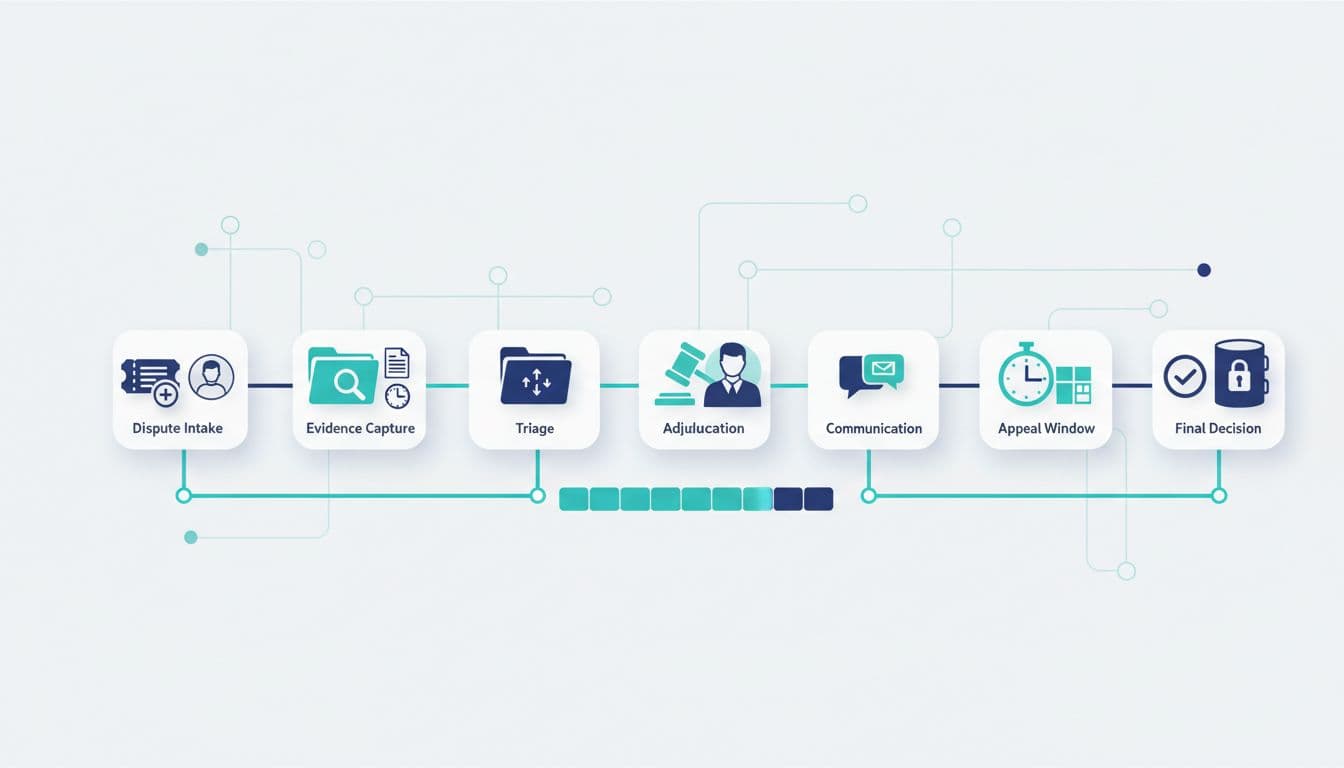
Disputes in tournaments tend to fall into three buckets: eligibility denial, fairness removals, and payout holds. A strong process treats disputes like a tracked delivery, not a messy email thread.
Step 1: Intake and case creation
Capture the complaint, tournament ID, timestamps, and what outcome the player wants. Confirm receipt and set expectations (timeline, what you need from them).
Step 2: Evidence capture (freeze the facts)
Pull and lock the data that can’t be re-created later:
- Entry logs and eligibility decisions
- Game logs (hand histories, round results, server events)
- Geolocation results at key moments
- Device and account linkage signals
- Chat and support transcripts
Step 3: Triage (severity and risk)
Route cases based on impact:
- Low impact: UI confusion, small prize tiers
- Medium: eligibility edge cases, bonus terms conflicts
- High: fraud flags, collusion removals, large payouts
Step 4: Adjudication (apply the rules, not opinions)
Review against published tournament terms and internal policies. If a rule changed mid-tournament, that’s a red flag. Rule versioning matters.
For game fairness questions, independent testing and certification can add credibility. Many operators reference labs and standards such as eCOGRA’s testing and certification services when explaining fairness controls.
Step 5: Communicate the decision (and the why)
Players don’t just want the answer. They want the reason. Share the decision, the policy basis, and what they can do next. Keep it short, clear, and consistent.
Step 6: Appeal window and final closure
Offer a defined appeal window for specific categories of disputes, then close with a final decision record and retention tag.
Conclusion: make verification part of the product, not a tax
When tournaments run clean, players notice. When they don’t, everyone notices. A practical iGaming tournament verification workflow combines eligibility gates, strong logs, and a calm dispute process that protects both your brand and your license.
If you’re building or tightening your tournament ops this quarter, start with one move: define the eligibility snapshot at entry and at payout, then make sure you can reproduce it on demand. That’s how trust becomes repeat play.

Adeyemi Adetilewa leads the editorial direction at IdeasPlusBusiness.com. He has driven over 10M+ content views through strategic content marketing, with work trusted and published by platforms including HackerNoon, HuffPost, Addicted2Success, and others.
