A deposit hits your iGaming cashier, the player wants fast access, and your payments team wants fewer chargebacks. One small control often decides how that story ends: payment method ownership checks.
This guide is for founders, risk managers, and operations leads building or scaling an iGaming brand. You’ll get a practical SOP you can hand to a team, clear proof examples for cards and e-wallets, and the awkward edge cases that trigger disputes, fraud, or compliance findings.
What payment-method ownership checks actually protect (and what they don’t)
Ownership checks confirm a simple thing: the person funding the account controls the card or e-wallet used. That matters because iGaming is a magnet for friendly fraud, stolen credentials, and third-party funding that can turn into AML issues.
A solid ownership process helps with:
- Chargeback defense: If the funding source is stolen or “borrowed,” disputes spike.
- KYC and AML alignment: Funding sources connect to player identity and, sometimes, source-of-funds reviews (see the difference in source of funds vs source of wealth).
- Safer withdrawals: It’s hard to justify paying out to a method you never tied back to the customer.
What it doesn’t do: it won’t “prove” the player is low risk on its own. Think of it like checking the shipping label matches the buyer. Helpful, but not a full fraud model.
If you’re aligning this with your wider KYC stack, it’s useful to compare against operator-focused guidance like KYC and age verification best practices.
A step-by-step SOP for payment method ownership checks (cards and e-wallets)
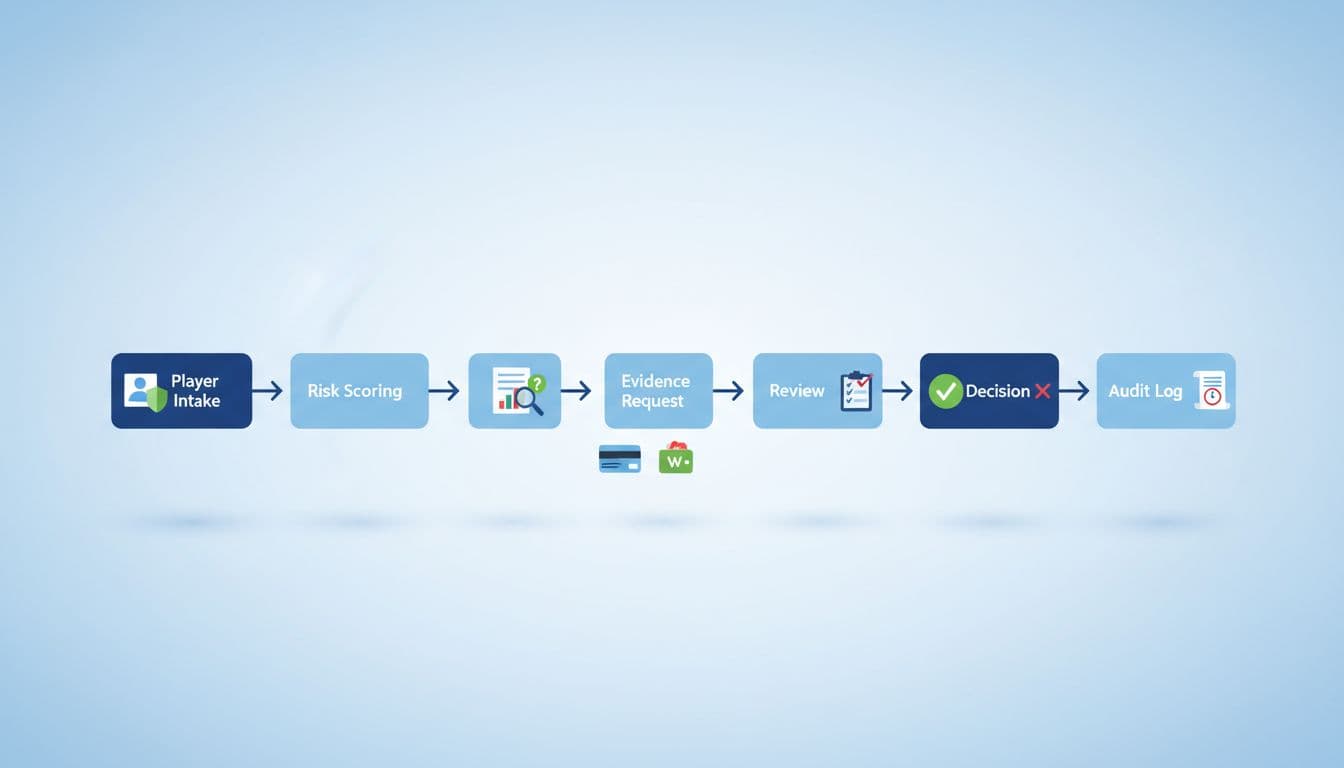
Step 1: Trigger the check (when and why)
Set triggers that match your risk appetite. Common triggers include first deposit, first withdrawal, a change in payment method, unusual deposit velocity, or a new device or location. Keep triggers consistent so players don’t feel singled out.
Step 2: Collect baseline data (without storing sensitive card data)
Capture what you need to compare later:
- Player account name, DOB, and address on file
- Payment method type (card vs e-wallet) and masked identifiers (last 4, BIN, wallet email)
- Deposit attempts, status, and timestamps
Never ask for full PAN, CVV, or raw credentials. Keep storage aligned with PCI scope. If you’re tightening internal payment practices, this Stripe PCI compliance guide is a good refresher on what pushes systems into heavier compliance.
Step 3: Risk score the transaction before asking for proof
Use simple rules before you add friction. Examples:
- Low risk: matched KYC name, stable device history, low amount, no failed attempts
- High risk: mismatched name, multiple cards, high amount, new device, rapid retries
Only request documents when the score warrants it. Otherwise, you train good customers to hate your cashier.
Step 4: Request evidence (with clear instructions and privacy guardrails)
Ask for one primary proof and one backup option. Tell players what to redact and what not to redact (more on that below). Give a deadline and explain what happens if they don’t respond.
Step 5: Review evidence using a “match rules” checklist
Your reviewer should verify:
- Name match: player name vs cardholder or e-wallet account holder
- Method match: last 4 digits, issuer, or wallet identifier matches the deposit record
- Recency: document is current (often within 90 days, depending on policy)
- Authenticity: no obvious edits, cropping patterns, or mismatched fonts
- Integrity: key fields visible, allowed redactions only
If something fails, record the exact reason and request a single re-upload. Don’t do endless back-and-forth.
Step 6: Decide, record, and apply controls
Outcomes usually fall into three buckets:
- Approve payment method, allow deposits and withdrawals to that method.
- Approve with limits, cap amounts until enhanced checks are done.
- Reject and restrict, block deposits, freeze withdrawals, or require an alternate method in the player’s name.
Log every decision with reviewer ID, timestamps, evidence type, and reason codes. That audit trail matters when disputes land months later.
For broader payments context in iGaming operations, this iGaming payments FAQ is a helpful list of real-world issues teams run into.
Proof examples that work (and what reviewers should reject)
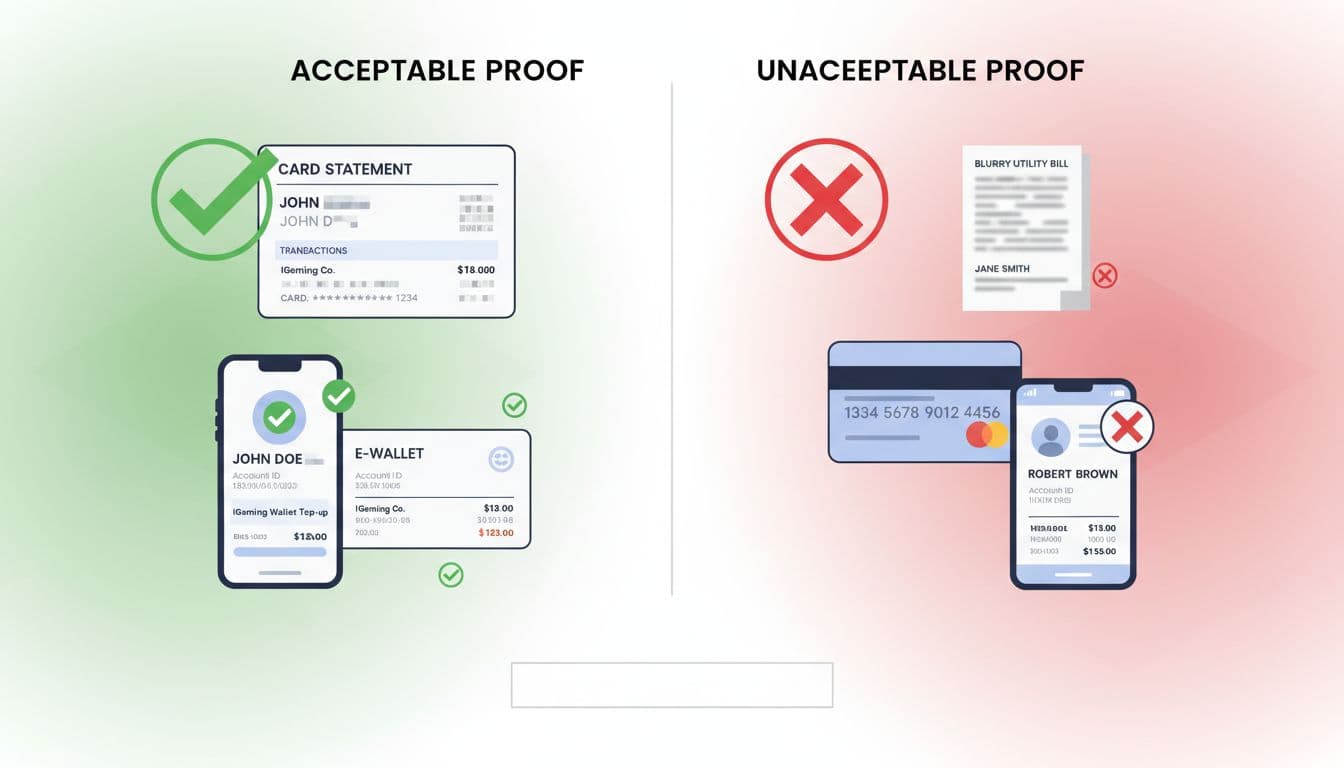
Ownership proof should answer two questions: “Who owns it?” and “Is it the same method used here?”
Cards: acceptable proof examples
Good options (ask for one):
- Bank or card statement showing cardholder name plus last 4 digits (PDF or screenshot)
- Issuer app screen showing card product, cardholder name, and last 4 (minimal sensitive data)
Redaction rule: last 4 digits can stay visible, full card number must not.
E-wallets: acceptable proof examples
Good options (ask for one):
- Wallet profile screen showing account holder name and wallet email or ID
- Wallet transaction history showing the deposit to your brand plus the same wallet ID
What to reject (most common)
- Blurry images, cropped corners, or photos of a different screen
- Proof where the name doesn’t match, even if the wallet email “looks right”
- Screenshots with heavy editing artifacts or missing key fields
- Documents showing full sensitive details (full PAN), which is a security risk
A quick reference helps reviewers stay consistent:
| Payment method | Best proof | Backup proof | Common reject reason |
|---|---|---|---|
| Card | Bank/card statement with name + last 4 | Issuer app screen | Name missing or digits don’t match |
| E-wallet | Wallet profile with name + wallet ID | Transaction history to merchant | Display name differs from KYC name |
If your platform uses electronic verification to support these checks, review an eKYC process outline like the Nuvei eKYC guide and map where ownership evidence fits.
Common edge cases (and a sane way to handle each)
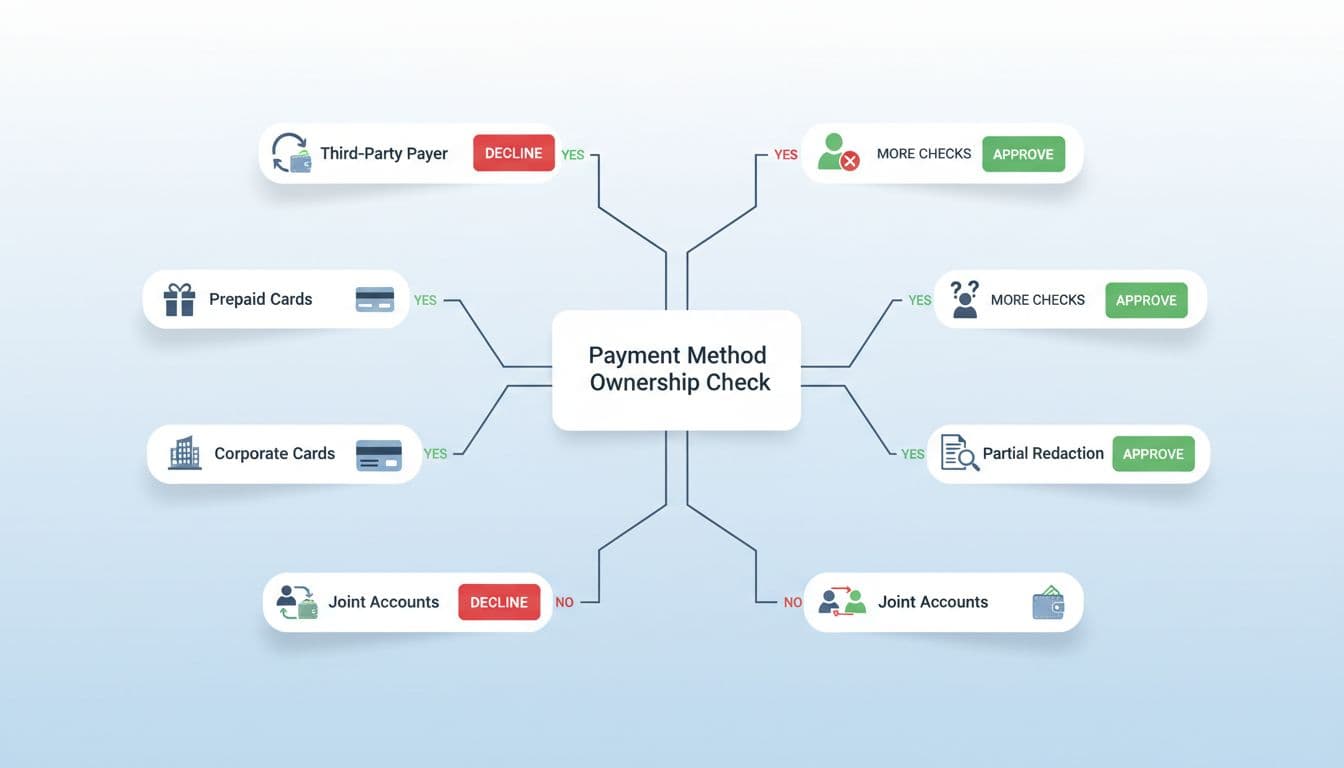
Edge cases are where teams drift into “gut feel.” That’s dangerous. Use written rules and stick to them.
Third-party payer (friend or family card/wallet)
Treat as high risk by default. In most setups, the safest rule is: deposits and withdrawals must use methods in the player’s name. If policy allows exceptions, require enhanced checks and set tighter limits.
Prepaid cards and gift-like instruments
Some prepaid products don’t show a cardholder name on statements. If you can’t tie it to the player, don’t approve it for withdrawals. Consider allowing deposits only, with strict caps, or block entirely.
Corporate cards
A corporate card can belong to a business, not a player. Unless your terms allow business accounts, corporate cards should usually be rejected for consumer play.
Name mismatch that’s explainable
Hyphenated names, maiden names, and shortened first names happen. Ask for one extra supporting document (government ID already on file, plus a statement) and document the rationale. Don’t accept “it’s my spouse’s card” as a name mismatch explanation.
Joint accounts
If the statement shows two names, match at least one to the player and make sure the deposit method details match (last 4 or wallet ID). Log it as a joint-account approval and monitor.
Partial redaction vs over-redaction
Players should redact sensitive numbers, but not the fields you need to match. If they black out the name or last 4 digits, it’s not usable. Give a clear re-upload request with an example.
Conclusion
Payment flows are where trust either holds up or breaks fast. When payment method ownership checks are documented, consistent, and backed by clear proof rules, you reduce chargebacks, protect withdrawals, and keep compliance reviews from turning into fire drills.
If your current process lives in someone’s head, turn the SOP above into a one-page checklist and start measuring re-upload rates and approval times. Those two metrics will tell you, quickly, whether your controls are working or just annoying the wrong players.

Adeyemi Adetilewa leads the editorial direction at IdeasPlusBusiness.com. He has driven over 10M+ content views through strategic content marketing, with work trusted and published by platforms including HackerNoon, HuffPost, Addicted2Success, and others.
