If your team can’t answer “who owns this alert” in 10 seconds, your iGaming AML escalation policy isn’t really a policy. It’s a hope.
In iGaming, alerts come in bursts, deposits move fast, and customer support is often caught in the middle. A working escalation policy does one main job: it turns messy signals into a clean handoff, with clear decision points, time limits, and accountable owners.
This guide shows how to write an escalation policy that staff will actually follow, with practical triggers, role ownership, and handoff notes that make audits less painful.
What a working iGaming AML escalation policy must do (and what it must not)
A good policy is like a fire alarm system. It doesn’t “prove” there’s a fire, it tells you when to stop normal operations and respond with urgency.
Your escalation policy should do three things:
- Define triggers that force a review or a senior decision.
- Assign owners for each stage (not departments, named roles).
- Standardize handoff notes so the next reviewer doesn’t start from zero.
What it must not do: list every risk ever, or leave “use judgment” as the only guidance. Judgment matters, but it needs rails.
For broader context on what regulators expect in gaming AML programs, the American Gaming Association AML best practices guide (PDF) is a useful benchmark for common control themes (risk-based approach, training, documentation, and reporting).
Step 1: Define escalation levels before you write triggers
Start by naming your levels in plain language. Most operators do well with three:
- Level 1 (Queue Review): standard alert, analyst can close or request info.
- Level 2 (Senior Review): elevated risk, needs compliance manager (or MLRO delegate) decision.
- Level 3 (MLRO Decision): potential reportable suspicion, sanctions concern, or urgent risk.
Write these levels into the policy first, because triggers should map to a level, not float around as random rules.
Step 2: Build clear triggers that people can spot in real time
Triggers should be observable from systems you already have: transaction monitoring, KYC/EDD, sanctions screening, device and account signals, and support tickets.
If you’re still tightening your monitoring logic, this iGaming transaction monitoring rules guide helps you translate risk patterns into alerts that don’t create nonstop noise.
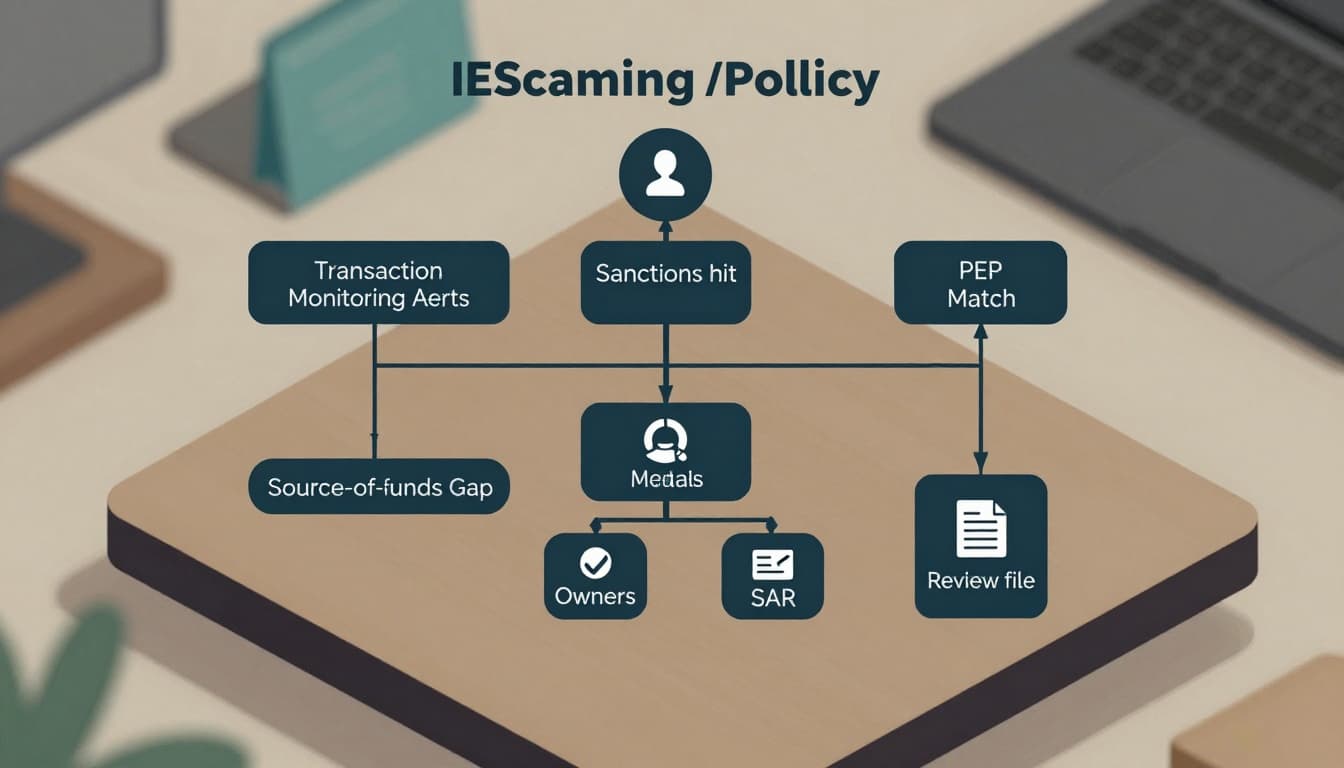
Here’s a practical trigger framework that works because it’s specific.
Core trigger categories to include
Sanctions and screening triggers
- Any sanctions match (even a possible match) that cannot be cleared quickly with documented evidence.
- Name and date-of-birth mismatch patterns that look like evasion (repeated attempts, multiple spellings).
PEP and high-risk customer triggers
- New PEP match after onboarding.
- PEP plus additional risk signal (high-velocity deposits, third-party funding, unusual withdrawals).
Source of funds and affordability triggers
- Source-of-funds request not satisfied by deadline.
- Documents received but inconsistent with player activity (example: low declared income, very high deposits).
Transaction behavior triggers
- Deposit-then-withdraw behavior with minimal play.
- Unusual cross-border behavior or high-risk jurisdiction exposure.
For a practical overview of how iGaming operators combine AML and sanctions screening expectations, see AML and sanctions compliance in iGaming.
A simple escalation mapping table
| Trigger example | Escalation level | Primary owner | Target response time |
|---|---|---|---|
| Standard transaction monitoring alert, no screening hits | Level 1 | AML Analyst | 24 hours |
| Deposit-then-withdraw pattern plus failed KYC step | Level 2 | Compliance Manager | 8 hours |
| Potential sanctions match not cleared, or credible suspicion | Level 3 | MLRO | 2 hours |
Keep the table short. If you need more, add an appendix, not more pages in the main policy.
Step 3: Assign owners with a RACI, then write the “handoff sentence”
A lot of escalation policies fail because “Compliance” is the owner. That’s like saying “the hospital” is the surgeon.
Assign ownership using roles. Then add a one-line handoff rule for each escalation, so the transfer is unmistakable.
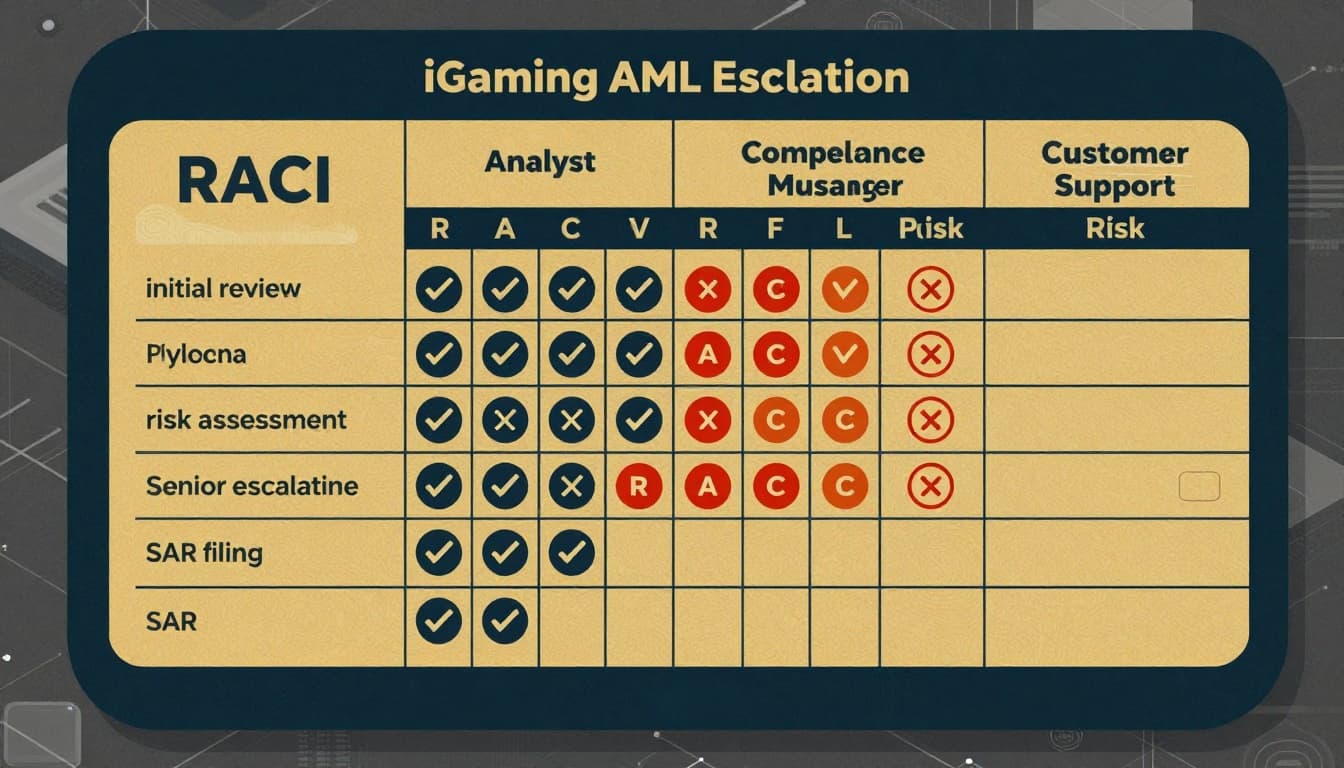
Example RACI (keep it realistic)
| Task | AML Analyst | Compliance Manager | MLRO | Payments/Risk | Customer Support |
|---|---|---|---|---|---|
| Triage alert and collect evidence | R | A | I | C | C |
| Decide on EDD request and limits | C | A/R | I | C | I |
| Decide on SAR/STR filing | I | C | A/R | C | I |
| Execute account restriction / payment hold | I | A | C | R | I |
| Request documents from customer | C | A | I | I | R |
Add a “handoff sentence” under each level in your policy, such as: “Level 2 cases transfer to the Compliance Manager with documented rationale, evidence links, and a stated next action.”
Step 4: Standardize handoff notes, so nobody re-investigates the same case
Handoff notes are where good programs win time back. Treat them like a case file cover sheet.
Minimum handoff fields that should be mandatory:
| Handoff field | What “good” looks like |
|---|---|
| Trigger | The exact rule or event (not “suspicious activity”) |
| Timeline | Key timestamps (deposit, withdrawal request, KYC prompts) |
| Evidence | Links or attachments, plus 1-line summary per item |
| Player context | Tenure, jurisdiction, risk rating, product used |
| Decision so far | What you did, what you ruled out, and why |
| Open questions | What the next owner must decide |
| Recommended next action | EDD, limits, closure, MLRO escalation, etc. |
If you use AI to draft summaries or extract document highlights, keep it controlled and reviewable. This is where explainable workflows matter, especially when you scale. For ideas on how finance teams apply GenAI in controlled ways, see generative AI applications in finance.
Step 5: Put time limits, stops, and “do not tip off” rules in writing
Escalation without deadlines becomes backlog.
Add two kinds of SLAs:
- First-touch SLA: when someone must open the case.
- Decision SLA: when a decision must be recorded (even if it’s “need more info”).
Also include explicit “stop” actions tied to levels, for example:
- Level 2: consider temporary limits (deposit cap, withdrawal review) while EDD is pending.
- Level 3: consider account freeze or payment hold, following your legal and regulatory requirements.
And write one clear rule on customer messaging. Customer support should have approved language that avoids tipping off while still being polite and consistent.
For examples of high-risk transaction control themes in gaming operations, this article on high-risk transactions and AML controls is a useful reference point, even if your workflows are digital-first.
Step 6: Make it usable, test it, and keep receipts
Before you publish the policy internally, run a tabletop test:
- Pick 5 real past cases (mix of false positives and true suspicion).
- Have a new team member follow the policy without help.
- Track where they hesitate, what fields they miss, and what isn’t clear.
Then update the policy and lock versioning. Auditors like to see not just a policy, but evidence it’s used.
Conclusion: Treat escalation like a relay race, not a debate
An escalation policy works when it removes uncertainty at the exact moment pressure hits. Clear triggers stop endless discussions, named owners prevent drift, and strong handoff notes keep the case moving without lost context.
If you want your iGaming AML escalation policy to stand up in audits and in busy weeks, write it so the next person can act fast, document well, and explain the decision later. Your future self will thank you, especially when the regulator asks, “Show us how this was handled.”

Adeyemi Adetilewa leads the editorial direction at IdeasPlusBusiness.com. He has driven over 10M+ content views through strategic content marketing, with work trusted and published by platforms including HackerNoon, HuffPost, Addicted2Success, and others.