A payment method isn’t just a checkout option; it’s a door into your business. Some doors come with cameras and ID checks. Others swing open with a code and a promise.
If you’re building controls around AML payment methods, you can’t treat cards, e-wallets, crypto, and vouchers the same way. Each one changes what you can verify, what you can monitor, and how fast bad activity can move.
This guide is for founders, operators, and marketers who want fewer nasty surprises: chargebacks, frozen payouts, regulator questions, or a sudden “we’re terminating your account” email.
Why the payment method choice changes your AML risk
AML controls depend on two things: identity and traceability. Payment methods shift both.
Cards often come with strong banking rails, but fraud and refund abuse can hide money movement in plain sight. E-wallets speed up peer-to-peer transfers, which is great for users and great for money mules.
Crypto can be transparent on-chain, yet still hard to tie to a real person. Vouchers and prepaid value are the closest thing to digital cash, which is why scammers love them.
Regulators have been clear that crypto and scam payments stay high on the radar. For example, FinCEN’s 2025 notice on crypto kiosks highlights how criminals use simple cash-to-crypto paths to move money fast (FinCEN Notice FIN-2025-NTC1).
A quick risk map by payment method (and what it does to your controls)
Here’s the simplest way to think about it: different rails give you different “receipts.”
| Payment method | What you usually get | What usually goes wrong | Control focus |
|---|---|---|---|
| Cards | Name, BIN data, dispute trail | Stolen cards, friendly fraud, and refund laundering | Velocity, 3DS, refund rules |
| E-wallets | Account history, device data, contacts | Mule networks, ATO, rapid layering | Behavioral monitoring, graph signals |
| Crypto | Public ledger, wallet activity | Sanctions risk, mixers, fast layering | Wallet screening, Travel Rule workflows |
| Vouchers | Often minimal identity | Scam funding, bulk buys, resale | Limits, step-up checks, redemption rules |
If you need a practical baseline for card acceptance and processor selection, this guide on merchant accounts that support e-wallets and cards is a useful companion.
10 control business ideas that match real AML payment method risk
1. Card velocity rules that adapt by customer tier
Summary: Treat a first-time buyer and a 12-month customer differently.
Why it’s valuable: Stops “hit-and-run” laundering patterns without hurting loyal users.
Who it’s for: E-commerce, SaaS trials, marketplaces.
How to start: Cap transaction count and total value per hour/day for new accounts, relax after a clean history.
Tools: Stripe Radar, Adyen RevenueProtect, Sift.
Example: A new account tries 8 small card charges, then a large one; you block the large step.
2. Refund and chargeback controls as an AML “exit gate.”
Summary: Refunds are a favorite cash-out route, so monitor them like withdrawals.
Why it’s valuable: Catches refund laundering and triangulation schemes early.
Who it’s for: Subscription businesses, ticketing, and digital goods.
How to start: Flag refunds to a different card, repeated partial refunds, or fast refunds after purchase.
Tools: Riskified, Signifyd, internal rules engine.
Example: Customer buys $900 in gift cards, requests a refund within 20 minutes to another funding source.
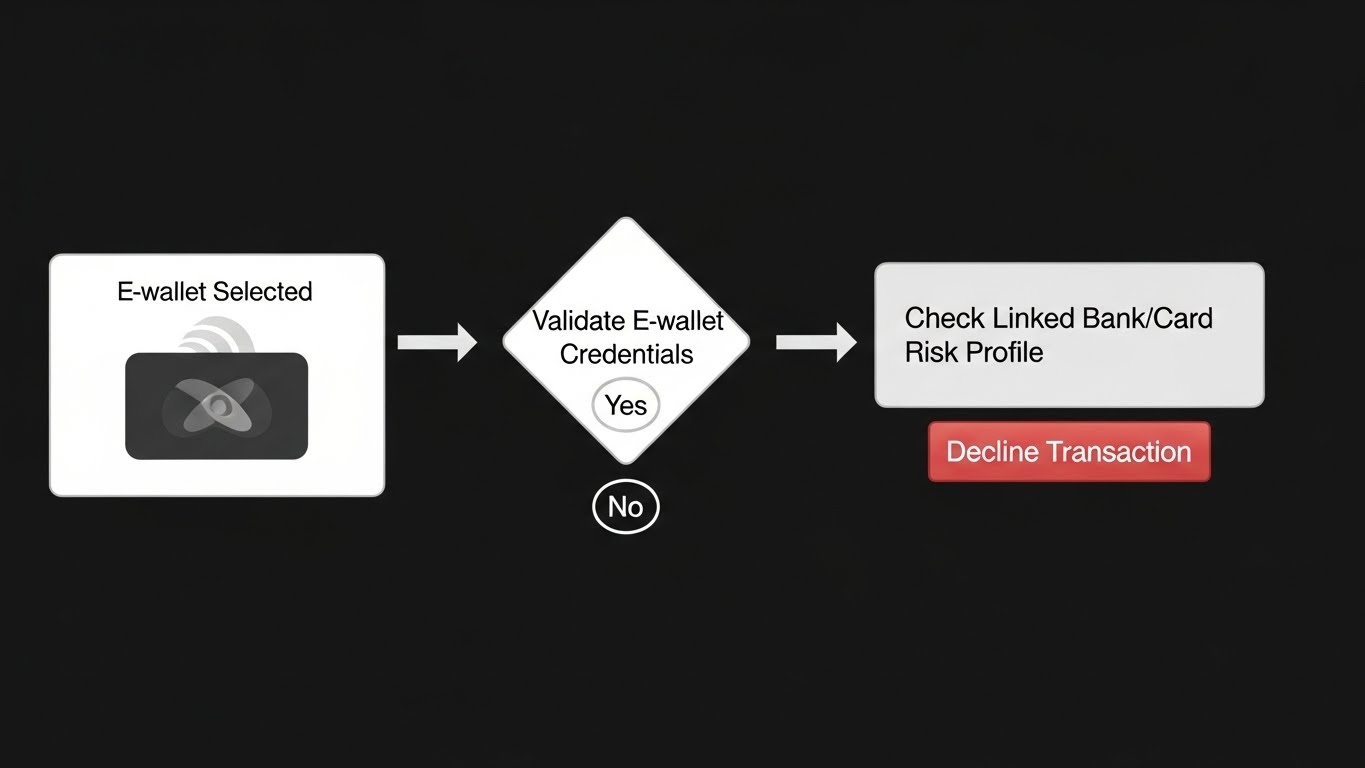
3. E-wallet name match plus “account age” gating
Summary: Don’t accept high-value wallet payments from brand-new wallet accounts.
Why it’s valuable: Reduces mule activity and synthetic identity use.
Who it’s for: Platforms that accept PayPal-like wallets, P2P apps, and gig payouts.
How to start: Require wallet holder name match to your profile, add limits until wallet age or history clears.
Tools: Persona, Alloy, Sardine.
Example: A new wallet with no history attempts a $2,500 purchase; you require ID and proof of address.
4. Device and session signals for e-wallet account takeover (ATO)
Summary: AML and fraud blend during ATO; treat it as both.
Why it’s valuable: Prevents criminals from using legit accounts to move dirty money.
Who it’s for: Any login-based checkout or stored wallet flow.
How to start: Flag new device plus password reset, plus first-time payee in a short window.
Tools: Fingerprint, Arkose Labs, AWS Fraud Detector.
Example: A long-time user logs in from a new country, adds a new wallet, sends three fast transfers, freezes, and reviews.
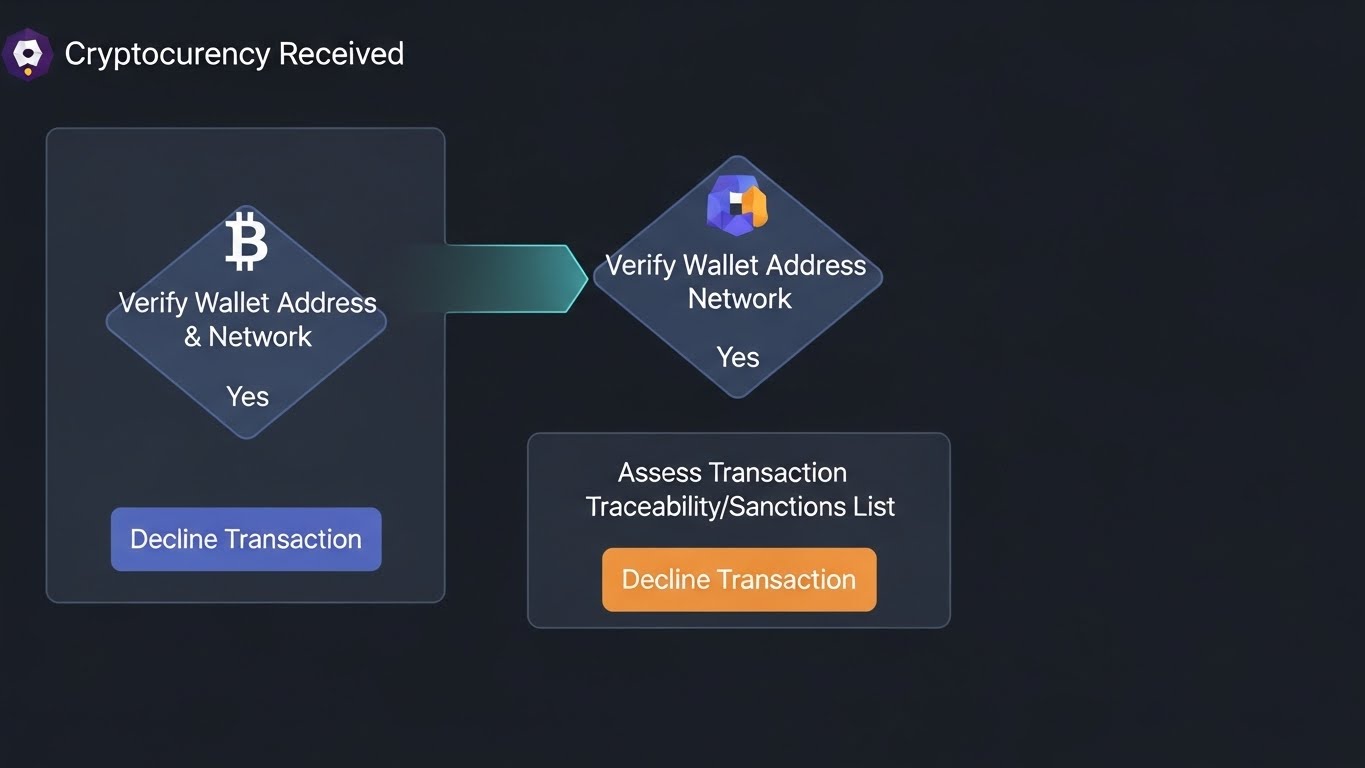
5. Crypto wallet screening before you accept deposits
Summary: Screen wallet addresses like your screen names.
Why it’s valuable: Cuts exposure to sanctions, known scam wallets, and high-risk services.
Who it’s for: Merchants accepting crypto, exchanges, and payroll in stablecoins.
How to start: Risk-score inbound addresses, block sanctioned exposure, and require EDD for high-risk clusters.
Tools: TRM Labs, Chainalysis, Elliptic.
Example: A deposit originates from a wallet linked to a known scam cluster. You quarantine funds and request the source of funds.
For teams setting up custody and internal controls, this roundup can help you evaluate the top crypto wallets for business payments.
6. “VASP-only” crypto withdrawals for new accounts
Summary: Route early withdrawals to regulated platforms first, then loosen later.
Why it’s valuable: Adds identity anchors during the highest-risk window.
Who it’s for: Apps with crypto cash-out, remittance, or creator payouts.
How to start: Allow withdrawals only to verified exchange accounts for 30 to 90 days, then permit self-custody based on risk.
Tools: Sumsub, ComplyAdvantage, KYT providers.
Example: A new user tries to withdraw to a fresh self-custody address, you require exchange proof or enhanced checks.
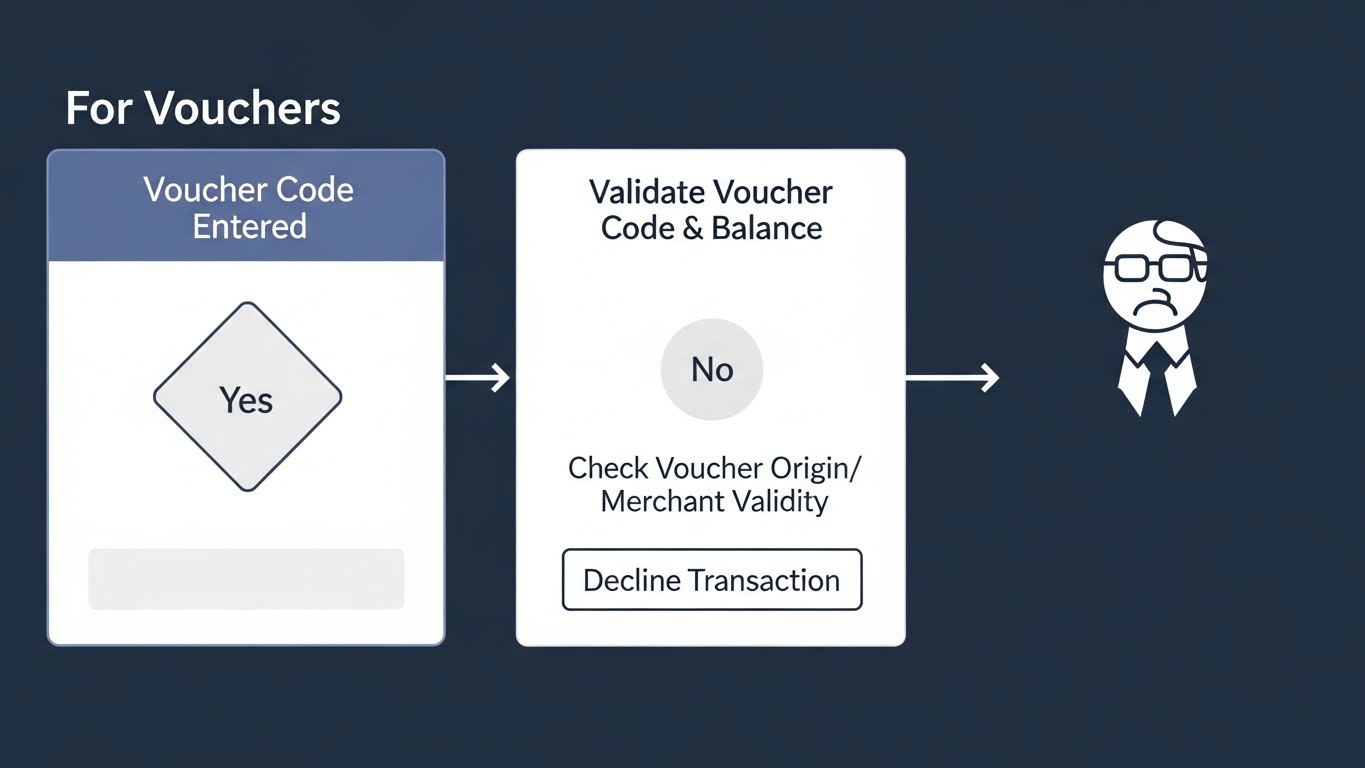
7. Voucher and gift card “bulk buy” tripwires
Summary: Gift cards behave like cash, so watch bulk patterns.
Why it’s valuable: Stops scam payment flows and money laundering.
Who it’s for: Retailers, gaming, digital marketplaces, and B2B incentive programs.
How to start: Limit count per card/account, block repeated purchases across multiple accounts from the same device/IP.
Tools: Forter, Feedzai, internal identity graph.
Example: Ten different accounts buy the same voucher SKU from one office IP in 15 minutes, you block and investigate.
8. Tiered KYC for prepaid and stored value (load limits tied to proof)
Summary: Increase limits only when the customer earns trust.
Why it’s valuable: Makes anonymous “placement” harder without blocking normal use.
Who it’s for: Fintech apps, prepaid programs, wallets with balances.
How to start: Set low default load limits, raise after document verification and ongoing behavior checks.
Tools: Onfido, Trulioo, Jumio.
Example: User can load $200 per day with email and phone, but needs an ID to load $2,000.
9. Cross-rail “same customer, many payment methods” monitoring
Summary: Criminals hop rails to break your view; you need one lens.
Why it’s valuable: Connects card payments, wallet transfers, and crypto activity into one story.
Who it’s for: Marketplaces and platforms with multiple payment options.
How to start: Build a unified customer risk profile, map devices, emails, payout accounts, and wallet addresses.
Tools: Segment, Snowflake, Databricks, case management system.
Example: A user pays by card, refunds to wallet, then buys crypto; the combined pattern triggers EDD.
10. Policy-backed escalation playbooks (so decisions are consistent)
Summary: Your team needs “if X, then Y” rules tied to risk, not vibes.
Why it’s valuable: Faster reviews, fewer missed SAR-worthy cases, cleaner audits.
Who it’s for: Any business with manual review or outsourced ops.
How to start: Define triggers per method (cards, e-wallets, crypto, vouchers), set hold times, and set evidence required to clear.
Tools: Jira/Linear for workflows, Unit21, Hummingbird.
Example: A high-risk crypto deposit plus rapid voucher purchases triggers a 24-hour hold and source-of-funds request.
If you’re onboarding customers who acquire crypto through exchanges, it helps to understand the compliance posture of major platforms.
How to choose the right controls for your payment stack
Use a short checklist before you add or expand a payment method:
- Traceability: Can you reliably link the payer to a real person or business?
- Reversibility: Can the payment be reversed (and abused) through disputes or refunds?
- Speed: How fast can value move from deposit to cash-out?
- Data access: Do you get device, location, and behavioral signals, or only a transaction ID?
- Regulatory exposure: Does this method pull in extra expectations (crypto, stored value, vouchers)?
If crypto is part of your stack, Treasury’s DeFi risk review is worth reading for context on where enforcement pressure tends to build.
Conclusion
If your controls don’t change when your payment mix changes, you’re driving with one headlight.
Cards push you toward refund and velocity controls. E-wallets demand behavior and network signals. Crypto needs wallet screening and strong withdrawal rules. Vouchers require strict limits and bulk detection.
Treat AML payment methods as a design decision, not a compliance afterthought, and your risk program becomes a growth asset instead of a fire drill.

Adeyemi Adetilewa leads the editorial direction at IdeasPlusBusiness.com. He has driven over 10M+ content views through strategic content marketing, with work trusted and published by platforms including HackerNoon, HuffPost, Addicted2Success, and others.
